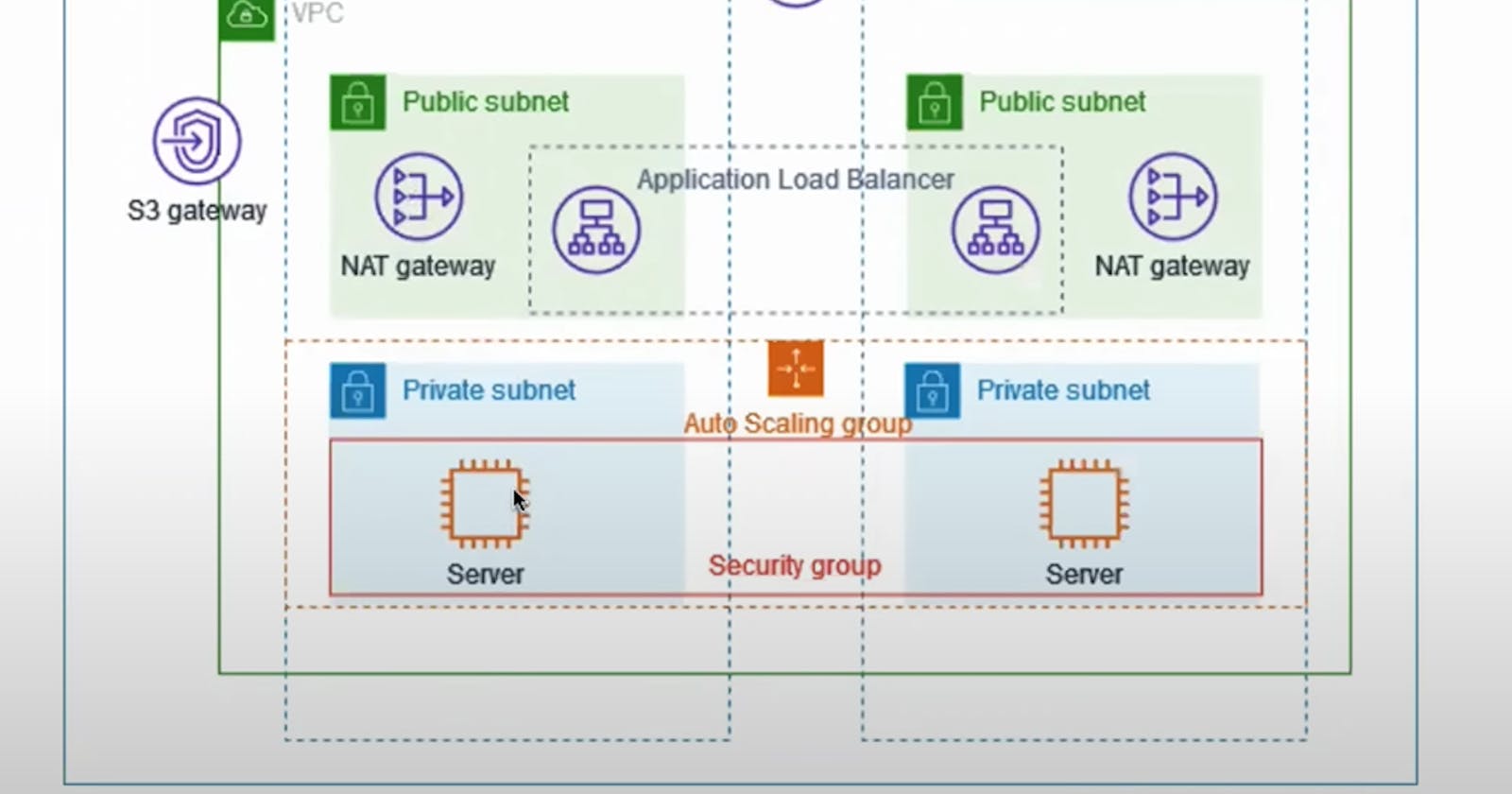
In this example demonstrates how to create a VPC that we can use for the production environment. By using auto-scaling groups, and load balancers we achieve resiliency. for security, we deploy a server in private subnets. server receives requests through the load balancer. the servers can connect to the internet by using a NAT gateway. we deploy the NAT gateway in both availability zones.
overview
the VPC has public subnets and private subnets in two availability zones. each public subnet contains a NAT gateway and a load balancer node. the servers run in the private subnets are launched and terminated by using an auto-scaling group and receive traffic from the load balancer. the servers can connect to the internet by NAT gateway.
why we need two availability zones because of flexibility and robustness. we need a load balancer because it is an essential components for distributing incoming network traffic across multiple instances (in this case, EC2 instances) to ensure high availability, improve fault tolerance, and optimize performance
auto scaling group - immediately takes a decision and increase our servers for n numbers.
Bastian host- By using a bastion host, you enhance the security of your infrastructure and better control remote access to your private instances. traffic goes to a private subnet through bastian host.
create a vpc- go tp vpc and create VPC by selecting vpc and more option.
Define the IP address ranges for your VPC using CIDR notation. choose availability zone 2, private subnet 2, vpc endpoint none.

2. create auto scaling group- got to ec2 and select auto scaling group. it can not be crated directly . use "use template". create security group, select vpc, add security gropu roles where my application requires. in my case i am opening SSH port 22 and custom tcp -8000.
in auto scaling configuration, select vpc, private subnets for ec2 instances. click on next and skip furhter parts and create .
Now verify 2 ec2 instances should be there running and subnet id should be empty becasue it is private instances.
install python application in ec2/ create bastain host - we use bastain servers /jump server because there is no public ip. and we can acess this private instance
got to ec2 - create a instance. with t2micro and add security groip allow ssh trafiic. select same vpc which we created. and launch instance.
ssh to bastian - for ssh we want a key value pair . so we will copy key value pair to private instance by using scp command.
copy pem file from >local to > bastian host-
scp -i <local path of pem file> ubuntu@<bastian host ip><path>:/home/ubuntu
now login to bastian host and see if the pem file copied ot not. ssh -i <pem file name> ubuntu@<ip of bastian>
now i need to login into a private instance
ssh -i <pem file> ubuntu@ <private ip of private ec2 instance>
create a normal index file and add html content to it.
run python server- python -m http.server 8000
application is running now.
so i logged into only 1 ec2 instance because while using load balancer, traffic goes to 1st then it will show a python application and while other it will show error.
create load balancer - we will create a load balancer and attach this instance to the target group.
configs are - give a name, scheme- internet-facing, ip adress- ipv4, add vpc which we just created in PUBLIC subnets. add SG.
Listners and routing - create target group- instance, give name, http -8000 , vpc
select private subnet and include as pending. create target group.
now add this target group to the load balancer
add listeners add port 8000 create load balancer.
go to load balncer and copy the DNS into browser
By completing this project, you'll have successfully built a secure VPC on AWS, with network security, routing, and access controls in place. This infrastructure can serve as a foundation for hosting various applications and services in a highly controlled and scalable environment.
Thanks for reading.... :)